CS475: Computer Networks
[ Course Info | Course Objectives and Goals | Resources | Instructors | Textbooks | Schedule | Grading | Course Policies | Course Details ]Welcome to CS475!
Course Info
- Course Number and Title: CS475 - Computer Networks
- Section A
- Credit Hours: 4 Semester Hours
- Credit Hours include "contact time" in the classroom and outside course work. It is expected that the sum of classroom time and outside course work time should add up to three times the listed credit hours per week.
- Course Webpage: https://BillJr99.github.io/Ursinus-CS475-Spring2023
- LMS (Canvas): Canvas
- Course Calendar: Import the course calendar into your favorite calendar app with this link!
- Class Notebook: Access our class notebook here! If you are unable to access the notebook, please let me know and I will share the document with your account.
- Academic Term: Spring 2022-23
- Term Start and End: through
- Course Prerequisites: CS274
- Class Meeting Locations and Times:
- Section A:
- s from 9:00 AM to 9:50 AM in PFA 007
- s from 9:00 AM to 9:50 AM in PFA 007
- s from 9:00 AM to 9:50 AM in PFA 007
- Midterm Exam:
- Section A: 2023/03/01 from 9:00 AM to 9:50 AM in Regular Class Period
- Final Exam:
- Section A: 2023/05/06 from 1:00 PM to 4:00 PM in Regular Class Period
- Course Description: Architecture and protocols of computer networks. Protocol layers; network topology; data-communication principles, including circuit switching, packet switching and error control techniques; sliding window protocols, protocol analysis and verification; routing and flow control; local and wide area networks; network interconnection; client-server interaction; emerging networking trends and technologies; topicsin security and privacy. This course will satisfy the College requirement for a capstone experience in the major. Prerequisite or co-requisite: CS-274. Offered in the spring of odd years. Three hours per week. Four semester hours.
Course Learning Objectives and Learning Goals
Learning Objectives
- To comprehend the design of a network protocol suitable for implementation
- To select appropriate network protocols at each layer of abstraction
- To write multithreaded code capable of multiplexing simultaneous socket I/O requests
Learning Goals
- To articulate network privacy concerns with a global context, and to identify practices and techniques to improve online privacy
- To differentiate between various models of network security, including authentication, authorization, and non-repudiation
- To identify and differentiate between approaches to fairness and quality-of-service on the Internet
The Questions
Throughout the course, we will be thematically guided by the Ursinus Questions:- What should matter to me?
- How should we live together?
- How can we understand the world?
- What will I do?
Specifically, we will collectively consider questions like:
- What happens when one requests a webpage from a popular website like Google?
- How can we organize the complexity of a global network into smaller components that we can understand, standardize, and optimize independently?
- How can we use standards to establish protocols to communiate over the Internet in ways that satisfy heterogeneous use cases and requirements?
- How are security and privacy built into the network?
Resources
Accommodations
Ursinus College and your instructor are committed to ensuring equal access and providing reasonable accommodations for all students. If you have, or think you have, a disability in any area such as, mental health, attention, learning, chronic health, sensory, or physical, please contact the Director of Disability Services.Ursinus College is committed to ensuring equal access and providing reasonable accommodations for students with disabilities. The Institute for Student Success works with students who have any kind of disability, whether apparent or non-apparent, learning, emotional, physical, or cognitive, and need accommodations to increase their access to this learning environment. I encourage you to reach out to the Director of Disability Services, Dr. Dee Singley to discuss about supports and accommodations you may need. Dr. Singley’s office is located in the Institute for Student Success in Lower Wismer. You can schedule a meeting with Dr. Singley by using this link: https://dsingley.youcanbook.me/, by emailing her at dsingley@ursinus.edu or by calling her at 1-484-762-4329. Students can also review accessibility and disabilities services on the ISS website.
Peer Coaching
The Institute for Student Success offers Peer Coaching that you can sign up for anytime. The Institute for Student Success connects students to the resources, activities, services, and programs that can help students be successful, thrive, and persist to graduation. They offer academic skills workshops, one-on-one coaching, tutoring, and more. Contact them at instituteforstudentsuccess@ursinus.edu or 610-409-3400.Early Alerts
From time to time, I may send academic early alerts through the college to you reagarding your academic performance or engagement in the class. These alerts are intended to help you engage in a way that will improve your ability to be successful. Should I send you an alert, I expect that you will follow up with me within 5 days to discuss your engagement on campus or in our class.Religious and Spiritual Life Observance Policy
Per the Religious and Spiritual Life Observance Policy, students who expect to miss classes, examinations, or other assignments due to religious observance may notify me two weeks prior to the observance. I will be happy to discuss reasonable alternatives with you.Wellness Center
Wellness Center resources are confidential and free to all students. Please consult the Wellness Center website for more information. As a student, you may experience a range of issues that can cause barriers to learning or reduce your ability to participate in daily activities. These might include strained relationships, anxiety, high levels of stress, alcohol/drug problems, feeling down, health concerns, or unwanted sexual experiences. The Wellness Center provides free short-term individual counseling, group therapy, and referral services that are confidential and are not a part of your educational record. Call Wellness at 610-409-3100 between 9:00-5:00, M-F. If you or someone you know is experiencing a crisis after hours, call Campus Safety at 610-409-3333. For a local resource, Montgomery County Mobile Crisis is available for 24/7 telephone support at (855) 634-HOPE (4673). The National Suicide Prevention Hotline also offers 24/7 support at 800-273-8255. As a student you may experience a range of issues that can cause barriers to learning, such as strained relationships, increased anxiety, alcohol/drug problems, feeling down, difficulty concentrating and/or lack of motivation. These mental health concerns or stressful events may lead to diminished academic performance or reduce a student’s ability to participate in daily activities. Ursinus College Wellness Center offers services to assist you with addressing these and other concerns you may be experiencing. If you or someone you know are suffering from any of the aforementioned conditions, you can learn more about the broad range of confidential mental health services available on campus via the Wellness Center by emailing wellness@ursinus.edu or calling 610-409-3100. If you are interested in more academic support, please contact the Institute for Student Success at instituteforstudentsuccess@ursinus.edu or 610-409-3400. If you find yourself struggling with your mental or physical health this semester, please let me know. I am one of many people here at Ursinus who care about you and your welfare. For example, the Wellness Center provides numerous health and counseling services, including free short-term individual counseling, group therapy, and referral services that are confidential and are not a part of your educational record. Contact the Wellness Center by emailing wellness@ursinus.edu or calling 610-409-3100.Center for Writing and Speaking
The Center for Writing and Speaking is available for one-on-one and group appointments to advise you as you revise your writing projects and presentations. They will even support your personal projects and extracurricular activities! Please feel free and encouraged to review any and all writing and speaking work from this class with them.Bear2Bear
The college recognizes that temporary financial hardships can impact students' access to course materials, as well as their access to opportunities on campus. Please be aware of the Bear2Bear fund, which has been established by donors to the college and provides special grants for students who have exhausted other sources of funding.Help Room
The Math Help Room (Pfahler 102) is a great place to go if you are struggling and is managed by the Institute for Student Success. Students who have previously taken the course will be there to help you with the assignments.Course Instructors and Student / Office Hours
| Role | Name and Contact Information | Student Hours / Office Hours |
|---|---|---|
| Professor |
William Mongan

Phone: 610-409-3410 E-Mail: wmongan@ursinus.edu Office: Pfahler Hall 101L |
|
Textbooks
| Required? | Title | Author | Edition | ISBN | Freely Available? |
|---|---|---|---|---|---|
| Required | An Introduction to Computer Networks | Peter L Dordal | 2nd Edition | 978-0133594140 | Online Version |
| Required | TCP/IP Tutorial and Technical Overview | Lydia Parziale et al | IBM Redbook | N/A | Online Version |
| Recommended / Supplemental | Computer Networking: A Top Down Approach | Jim Kurose and Keith Ross | 8th Edition | N/A |
Course Schedule
| Week | Date | Title | Readings | Deliverables Handed Out | Deliverables Due |
|---|---|---|---|---|---|
| Week 1 | Course Overview |
|
|||
| Week 1 | Sending Packets |
|
|||
| Week 2 | Motivating Examples: nslookup, HTTP, Traceroute |
|
|||
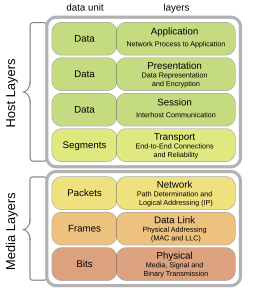
| Week 2 | Networking: A Layered Approach |
|
|||
| Week 2 | Socket Programming |
|
|
||
| Week 3 | Socket Programming | ||||
| Week 3 | Multithreaded Socket Programming |
|
|||
| Week 3 | Multithreaded Socket Programming | ||||
| Week 4 | The Physical Layer: Considerations |
|
|||
| Week 4 | TDMA with CSMA and ALOHA |
|
|||
| Week 4 | CSMA and ALOHA |
|
|||
| Week 5 | Ethernet | ||||
| Week 5 | Wi-Fi with FDMA and CDMA Wireless Protocols | ||||
| Week 5 | The Link Layer | ||||
| Week 6 | Switching | ||||
| Week 6 | From Bits to Packets |
|
|||
| Week 6 | The Network Layer and IPv4 | ||||
| Week 7 | IPv4 Addressing and Subnets | ||||
| Week 7 | IPv4 Addressing and Subnets |
|
|||
| Week 7 | IP Multiplexing with NAT | ||||
| Week 9 | Outside Address Lookups with DNS |
|
|||
| Week 9 | Inside Address Lookups with ARP |
|
|||
| Week 9 | Dynamic Configuration with DHCP | ||||
| Week 10 | ICMP and Ping | ||||
| Week 10 | IPv6 |
|
|
||
| Week 10 | VPN and Tunneling | ||||
| Week 11 | Routing | ||||
| Week 11 | Distance Vector Algorithms | ||||
| Week 11 | Hierarchical Routing |
|
|
||
| Week 12 | Routing at Scale: BGP |
|
|
||
| Week 12 | The Transport Layer: Considerations |
|
|||
| Week 12 | Basic Transport Services with UDP |
|
|||
| Week 13 | Coordinating Transport Services with TCP | ||||
| Week 13 | TCP | ||||
| Week 13 | TCP Sliding Window Protocols |
|
|||
| Week 14 | Congestion Management with TCP | ||||
| Week 14 | Application Layer Protocols |
|
|||
| Week 14 | HTTP and SMTP | ||||
| Week 15 | Security and Privacy |
|
|||
| Week 15 | Security and Privacy | ||||
| Week 15 | Security and Privacy with Public Key Cryptosystems |
|
|||
| Week 16 | Review | ||||
| Week 16 | Review |
|
- Add Deadline:
- Drop with a W Deadline:
- CoSA:
Grade Breakdown
Letter grades will be assigned on the scale below at the end of the course. "Grade grubbing" is not conducive to professional practice; every assignment has or will have very precise expectations and point breakdowns, and I will evaluate submitted work carefully according to these standards. I will also return assignments in a timely manner, and the running weighted grades will be updated frequently. Therefore, I expect a commensurate level of respect from you. In sum, you should know where you stand at all times, there will be plenty of opportunities to improve your standing, and there should be no surprises at the end of the course.Grading Table
| Item | Weight |
|---|---|
| Programming Assignments | 25% |
| Labs | 40% |
| Midterm Exam | 15% |
| Final Project | 10% |
| Class Participation and Quizzes | 10% |
Letter Grades
| Letter | Grade Range |
|---|---|
| A+ | 96.9-100 |
| A | 93-96.89 |
| A- | 89.5-92.99 |
| B+ | 87-89.49 |
| B | 83-86.99 |
| B- | 79.5-82.99 |
| C+ | 77-79.49 |
| C | 73-76.99 |
| C- | 69.5-72.99 |
| D+ | 67-69.49 |
| D | 63-66.99 |
| D- | 59.5-62.99 |
| F | 0-59.49 |
Course Policies
Classroom Environment and Inclusivity Standards
My goal is to foster a environment in which students across all axes of diversity feel welcome and valued, both by me and by their peers. Axes of diversity include, but are not limited to, age, background, beliefs, race, ethnicity, gender/gender identity/gender expression (please feel free to tell me in person or over e-mail which pronouns I should use), national origin, religious affiliation, and sexual orientation. Discrimination of any form will not be tolerated. Furthermore, I want all students to feel comfortable expressing their opinions or confusion at any point in the course, as long as they do so respectfully. As I will stress over and over, being confused is an important part of the process of learning computer science. Therefore, I will not tolerate any form of put-downs by one student towards another about their confusion or progress in the class. Learning computer science and struggling to grow is not always comfortable, but I want it to feel safe. Much of this material is probably new to everyone, and those with some prior experience likely recall a time when it was new to them, too. Remember that this is not a competition: helping others to grow is itself a richly rewarding professional development opportunity. In order to allow for equitable access to class for students who may be attend and participating remotely, I may record our class sessions. These recordings will only be available on our Canvas site. I will announce that we are recording in the beginning of any classes of this kind; out of respect and privacy for me and all class members, please do not download, copy, or redistribute class recordings.Online Communication Policy
Since this is a class-wide communication, the following rules apply to message groups and electronic communications:- Students are expected to be respectful and mindful of the classroom environment and inclusivity standards.
- They are equally applicable to a virtual environment as they are in class.
- Students are not permitted to share direct answers or questions which might completely give away answers to any homework problems or labs publicly on Microsoft Teams. When in doubt, please send me a direct message there.
- I will attempt to answer questions real time during student / office hours. Otherwise, I will make every attempt to respond within 24 hours. Of course, students can and should still respond to each other outside of these intervals, when appropriate!
- Students may ask anonymous questions.
Course Management Systems: Canvas, Microsoft OneNote, and Microsoft Teams
We will be using Canvas to post all of the grades. For the most part, we will submit work using Canvas as well. For class activities and notes, we will be using OneNote, and for other discussions and announcements for the course, including messaging me directly with questions, we will use Microsoft Teams. OneNote and Teams are linked to your Office suite through Ursinus, so you are automatically enrolled. There you can ask and answer questions about the lecture content and assignments.Since it is likely that students will have similar questions, it is much more efficient for me to answer them there so the whole class can see the answer, so it is possible that I will ask you to re-send a question publicly that I get in an e-mail. If you'd prefer, I could anonymize the question as well, but I'd like you to have the opportunity to post it so that you are credited with having such a good question!
Collaboration Policy and Academic Integrity Policy
Communication between students is allowed (and encouraged!), but it is expected that every student's code or writeups will be completely distinct! Please do not copy code off of the Internet (repurposing code from the Internet will probably make it harder anyway because the assignments are so specialized). Please cite any sources in addition to materials linked from the course website that you used to help in crafting your code and completing the assignment.See the Course Management page in the Faculty Handbook for an explanation of college policies on plagiarism and other academic honesty violations.
To encourage collaboration, students will be allowed to choose one "buddy" to work "near" during the assignment. Students are still expected to submit their own solutions, but they are allowed to provide substantial help to their designated buddy, and even to look at the buddy's code during the process. Students must indicate their buddies in the README upon assignment submission. Please let me know if you would like a buddy but are having trouble finding one.
Below is a table spelling out in more detail when and how you are allowed to share code with people (table style cribbed from Princeton CS 126).
Please Note: The terms "exposing" and "viewing" exclude sending or ingesting electronically, which would be considered copying. Exposing and viewing are normally done in the context of in-person working or in the help room. In addition, "Other People" includes internet sources!
| Your Buddy | Course Staff | Course Grads | Classmates | Others | |
|---|---|---|---|---|---|
| Discuss Concepts With | OK | OK | OK | OK | OK |
| Acknowledge Collaboration With | OK | OK | OK | OK | OK |
| Expose Your Code/Solutions To | OK EXCEPT FOR Assignments |
OK | OK | NO | NO |
| View the Code/Solutions Of | OK EXCEPT FOR Assignments |
OK | NO | NO | NO |
| Copy Code/Solutions From | NO | NO | NO | NO | NO |
If the work you submit appears to be copied from previous work or the collaboration policy has been violated in any way (including working with more collaborators or "buddies" than the course deliverable specifies) according to the College Academic Honesty policy, regardless of intent, then it may be an academic dishonesty case, and it will be referred to the Associate Dean for Academic Affairs. I am required to make this report in every occurrence, so it is best to speak with me first if there are any questions about the policy or expectations. You should feel free to have these conversations with me anytime prior to making your submission without fear of penalty. Finally, aside from the collaboration policy here, it is expected that your work is your original work. You must cite any collaborations or references that you use. You may have a friend or relative with computing experience, but they should not do your assignments, labs, etc., for you.
Flexible Submission Policy
In the absence of accommodations arranged in advance with the instructor or college, all assignments are due at 10:59PM Eastern Time on the date(s) stated on the schedule. Assignments will be accepted without prior permission following this time with a points deduction of 4% per day if submitted before 10:59 PM Eastern Time on the day submitted. Each student will receive a total of 10 "slack days" for the semester with which to waive these grade reductions; for example, one assignment may be submitted 10 days late, or two assignments may be submitted 5 days late, with no grade reduction. Extra credit will not be awarded for assignments submitted under the flexible submission policy. Students with accommodations will receive additional "slack days" as specified within the accommodations letter; however, some deliverables cannot be subject to accommodations due to the time-sensitive nature of the assignment (for example, group assignments, presentations, and course surveys). Students who add the class late shall receive additional slack days equal to the number of days between the start of classes and the first date that approval is given or that class is attended (whichever occurs first). Under no circumstances (including accommodations) can late work be accepted after the final class meeting, nor during final exams week, nor after the exam.A Word About Submitting Work On-Time
Managing your time and pacing yourself consistently are crucial to your academic success. In professional practice – and in the spirit of the Ursinus Question “how should we live together?” – others will depend on you and will build upon the work you create. In the classroom, these interactions are modeled in the form of group projects and activities, and also in the form of cumulative course content that builds upon itself thematically throughout the semester. Research indicates that self-imposed or flexible deadlines does not lead to optimal scheduling [1], which, in turn, can lead to a compounding of overdue work across multiple classes. In addition, extensions to or prolonging of assignment deadlines has been shown to yield a detrimental appearance of complexity [2]: we tend to believe that assignments with longer durations are more difficult, and can find it more difficult to get started due to the anxiety that results. Your professor has established a schedule and procedure for completing and submitting classwork that complements the topics being covered during the semester. The specific details of that schedule and of those procedures may vary from instructor to instructor, depending upon the unique needs and instructional approach of the class. These details are specified in the course syllabus, and because those details have been designed thoughtfully and intentionally to best enable your consistent engagement with the class, the guidelines in that syllabus pertaining to engaging in the course, completing work, and posting grades (including a grade of incomplete) shall be considered effective policy for the course. Regardless of the implementation details from one course or from one instructor to another, these instructional designs are intended to enable you to engage with the course in a healthy and consistent manner, to manage your time effectively between your class, your other classes, and your extracurricular activities, and to better position you for success in class and beyond. (References: [1] Ariely, Dan, and Klaus Wertenbroch. “Procrastination, Deadlines, and Performance: Self-Control by Precommitment.” Psychological Science, vol. 13, no. 3, May 2002, pp. 219–224, doi:10.1111/1467-9280.00441. [2] Meng Zhu, Rajesh Bagchi, Stefan J Hock, The Mere Deadline Effect: Why More Time Might Sabotage Goal Pursuit, Journal of Consumer Research, Volume 45, Issue 5, February 2019, Pages 1068–1084, https://doi.org/10.1093/jcr/ucy030.)Grade Posting Policy
Feedback and grades will be provided frequently, generally within one week of the due date of any deliverable, and no more than two weeks following the due date. Inquiries seeking a change of grade must be made within 7 days of the posting of the grade in question, including the posting of a reduced grade for a missing submission. Final grades are due within 48 hours of the final exam (or last class scheduled meeting in a class with no final exam); grades are not subject to change (including a change from a posted grade to a grade of incomplete) once submitted to the college.Incomplete Policy
A grade of I may only be granted by permission of the Office of the Dean. A petition to the Office of the Dean will only be made upon written request by the student, including all information requested by the Office of the Dean. Requests for a grade of I will only be made in situations where such a request is warranted. Specifically, the student's grade must be passing at the time the request is made. A petition for a grade of I will not be considered if an academic alert was submitted by the instructor prior to the course Drop with a W (withdraw) deadline.Title IX
Title IX is a federal law, under which it is prohibited to discriminate, harass, or commit misconduct on the basis of gender or sex. The Title IX Coordinator is available to receive inquiries and to investigate allegations in this regard. As a professor, I am a mandatory reporter under Title IX, and am required to report disclosures made to me related to Title IX.Inclement Weather and Class Cancellation Policy
In the event that the College closes due to inclement weather or other circumstances, our in-person class sessions, student / office hours, labs, or other meetings will not be held. I will contact you regarding our plan with regard to rescheduling the class or the material, any assignments that are outstanding, and how we can move forward with the material (for example, any readings or remote discussions that we can apply). If necessary, I may schedule online virtual sessions in lieu of class sessions, and will contact you with information about how to participate in those. I will communicate this plan to the department so that it can be posted on my office door if it is feasible to do so. This policy and procedure will also apply in the event that the College remains open but travel conditions are hazardous or not otherwise conducive to holding class as normal. Should another exigent circumstance arise (for example, illness), I will follow this policy and procedure as well.Student Perception of Teaching Questionnaire (SPTQ)
I will be soliciting student feedback through the SPTQ and possibly through other forms of commentary. This feedback greatly assists me and the department as we develop our courses and overall curriculum for this program. This course has benefitted from the feedback of those students who took the course before you, and your feedback will help maintain and improve the course for those to follow. I strongly encourage you to participate in this important and valuable process.Syllabus Subject to Change
I will do my best to provide all relevant information about the course on this syllabus. Sometimes, exigent circumstances, the pace of the class, or other circumstances will warrant minor revisions to the syllabus. For example, inclement weather or other campus closure might affect the course schedule and assignment deadlines; in addition, I may find that the class benefits from spending more time on a particular topic, and adjust accordingly. Although I try to avoid rescheduling student / office hours, it may become necessary from time to time to accommodate other events in the College. Should any revisions be necessary, I commit to making any revisions in my estimation of the best interests of the class, and commit to communicating those changes to you as soon as I make them.Course Details
Overview
Computer Networks study interconnected computing systems at scale from many different perspectives. Moving a bit from one computer to another over the Internet is a complex process. The bit must travel to its destination from one computer to another, which must have some way of knowing where that bit is trying to go so that it can be moved along the right path. Wireless communications (and even wired connections) are subject to noise and interference that may corrupt the bit as it transits between any two of those computers. We need ways to manage these destination addresses, optimal pathways, and mechanisms to detect corrupted messages. Sometimes, computers might become too overworked to forward your message, and they can be lost: worse yet, we cannot communicate this situation back to the sender (after all, if we had the resources to do so, we could have just forwarded the message properly!). The sender, then, needs a way to ensure that their message was received, and received in-tact. Ideally, we would do so efficiently: if new, faster paths to the destination appear (sort of like new expressways on the interstate highway system), we’d like to find out about them and utilize them, traffic permitting. Even then, we need to define what those bits represent: an e-mail, a webpage, a function call, or data like a shopping cart. And beyond all this, we need a mechanism to enable these communications to occur privately and securely: we want to ensure that the sender and receiver can validate one another’s identity and privilege. To facilitate all of this, we organize the study of computer networks into a “layered” model, in which we investigate each of these concepts independently of the others. In fact, networks are implemented according to this layered model, which greatly simplifies the apparent complexity of the network as a whole: we implement an independent algorithm for each concept, and they interact only as much as is required (typically, only with one or two neighboring algorithms, which, in turn interact with their immediately adjacent layers).
Homework
Labs
Every week, we will have a lab session where students get a chance to practice concepts we just learned in a safe and collaborative environment. Tasks will be given that serve as warm-ups for the larger assignments, and final submissions will be graded on a scale from 0 to 2. Students will have a chance to refine their submissions until the Friday of every week, and there will be help from the Lab T.A.s listed above.
Assignments
The bulk of the grade in the course will be earned by completing individual programming assignments. Be sure to start them early! Note that collaboration and sharing rules differ slightly for labs and assignments.
Classroom Participation
Group Work [1]
In addition to ordinary participation that follows the natural rhythm of a lecture, most days there will be at least one followup problem, which is a question that follows on the heels of newly presented material. Students will split into groups of 2 and try to write some code to address a particular problem. When a group of students believe they have figured out the answer, they raise their hand. The other students can continue to work while I verify that the answer is correct. If the answer is correct, the students present the answer to the class. If the group is not correct upon my checking, then the groups continue this process until one gets it correct.
Other ways to help your fellow classmates in class are as follows:
- Helping to teach a student a topic during office hours.
- Certain calls for participation in class
- Particularly helpful or insightful messages on Microsoft Teams
- Finding mistakes in the book or on the assigned homework and labs
Class Participation and Classroom Etiquette [1]
For classroom attendance, the following rules apply:
- Please be attentive during class. There will be class exercises that involve coding, but class time should be used for learning computer science. It is imperative that technology be used for this purpose during our class time together. Alternatively, please try to think of this as a safe space away from social media. We could all use a break, and we are fortunate to have a good excuse to make that space.
- Please follow common courtesy. For instance, you can bring food and drink as long as it’s not distracting, but please clean up after yourself if you do. Our janitorial staff deserves the utmost respect and help with their job.
- In-class exercises and “low stakes” activities will take place individually and in groups to assess our progress together. These exercises will be given both synchronously (for example, in-class activities, pair programming exercises) and asynchronously (for example, pre-lab exercises, peer code reviews, book surveys) and will be graded on a participation basis. These are given equal weight and form the basis of the class participation score.
- If a class session is remote, please feel free to make choices that make you most comfortable. For example, I will record these sessions for students who cannot make the session or for those who would benefit from a review of the material. I’d encourage you to enable your video feed if it is available, but if you need leave your video off, you feel free to do so; however, if you find that this becomes necessary on a prolonged basis, please see me to discuss. Please keep your microphone on mute to avoid background noises while others are speaking; however, please do not feel “mic fright” about unmuting to speak up and participate anytime. If, however, you would prefer to communicate via the chat interface (either exclusively or in combination with your audio/video), you should feel free to do that. Whether in-person or remote, all I ask is that you engage as best you can; the material is challenging but fun, and we’re all here to learn new things together.
-
This introduction is adapted from Dr. Tralie’s CS173 Course Syllabus. ↩ ↩2