CS475: Computer Networks - The Network Layer
Activity Goals
The goals of this activity are:- To describe the roles and responsibilities of the Network Layer
- To explain network layer protocols including NAT, DNS, DHCP, ICMP/Ping
- To differentiate between addressing models IPv4 and IPv6, and how to tunnel between them
- To explain the need for multiplexing on IPv4 networks with private subnets, and the role of NAT and port forwarding
- To define subnets of arbitrary size using CIDR subnetting and class A/B/C subnets
- To differentiate between a switch and a router
- To explain the functionality of a VPN over existing network infrastructure
Supplemental Reading
Feel free to visit these resources for supplemental background reading material.The Activity
Directions
Consider the activity models and answer the questions provided. First reflect on these questions on your own briefly, before discussing and comparing your thoughts with your group. Appoint one member of your group to discuss your findings with the class, and the rest of the group should help that member prepare their response. Answer each question individually from the activity on the Class Activity Questions discussion board. After class, think about the questions in the reflective prompt and respond to those individually in your notebook. Report out on areas of disagreement or items for which you and your group identified alternative approaches. Write down and report out questions you encountered along the way for group discussion.Model 1: The IP Packet Header
Questions
- What types of protocols can we denote in an IP Packet?
- What is the purpose of the Version field?
- What is the purpose of the TTL field?
- What addresses are placed in the source and destination fields? How might this differ from the MAC addresses used in the Link Layer header?
- What, if any, information helps the IP protocol to provide throughput control, error correction, or packet ordering? What, in your own words, is "Best Effort" quality-of-service?
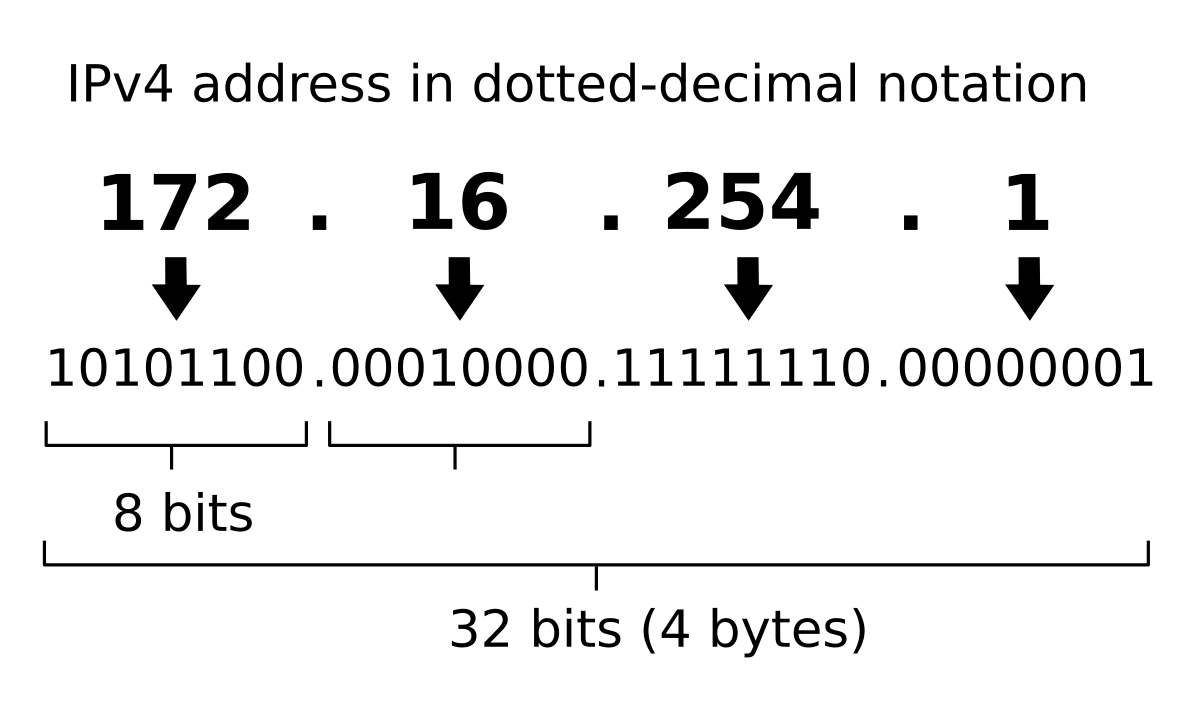
Model 2: IP Addressing
Questions
- How large is an IPv4 Address? What is the largest and smallest value that can be represented by each octet?
- How many IPv4 addresses can be allocated on the Internet?
Model 3: IP Fragmentation
Questions
- IP fragments are sized in 8-byte blocks. Which fields of an IP packet are modified to indicate that this packet is a fragment, and what part of the overall packet it represents?
- Another layer of the network stack can perform fragmentation in order to regulate transmission rate. However, no information is retained at this layer about network throughput and performance. Therefore, what do you think is the purpose of fragmentation at this layer?
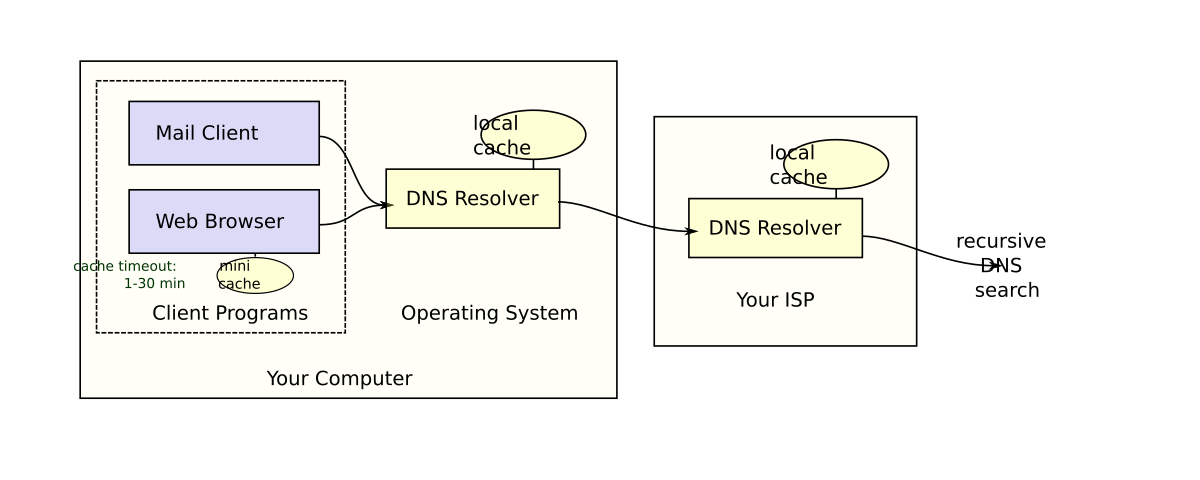
Model 4: Address Lookups with DNS

Public Domain, Link

By Lion Kimbro - Own work, Public Domain, Link
By Lion Kimbro - Own work, Public Domain, Link
Questions
- How many DNS servers are there? How is the DNS "database" stored on the Internet?
- If DNS is distributed, how does one locate the appropriate DNS server corresponding to the network being sought?
- What is the difference between a recursive DNS lookup and an iterative one?
Model 5: Subnetting
Questions
- What is the relationship between the number of node addresses and the subnet number following the network address?
- Write out one of the IP addresses in binary. Given the number of node addresses available in each subnet, which bits in the address represent the network address, and which represent the node address?
Model 6: Network Configuration with DHCP
Questions
- What information do you expect to be included in a DHCP packet?
Model 7: Port Forwarding and Network Address Translation (NAT)

By Michel Bakni - This file was derived from:Server symbol-blue.svgNetwork cloud symbol.svgWorkstation symbol-Blue.svgRouter symbol-Blue.svgWendell Odom (2013) (in English) Cisco CCENT/CCNA ICND1 100-101 Official Cert Guide (Academic ed.), Pearson Education, Inc., p. 582 ISBN: 1587144859., CC BY-SA 4.0, Link

Questions
- What is the relationship between a host's IP address and the externally-facing IP address to the network?
- How does one address a packet to a host with a private IP address behind a NAT network?
- When a packet arrives at the local network's router, what additional information is needed to identify which private node should receive the packet?
- What are some of the compromises made by NAT? What are the benefits?
- What would render NAT unnecessary?
Model 8: The Internet Control Message Protocol (ICMP)

By Michel Bakni - (2012) TCP/IP Illustrated Volume 1 (Second ed.), Pearson Education, Inc., p. 355 ISBN: 0321336313., CC BY-SA 4.0, Link
Questions
- What type and code are used for an ICMP Ping echo request and reply?
- What type and code are used for an ICMP TTL Expired message?
- What other control messages are supported by ICMP?
- Why can't we rely on ICMP messages to regulate transmissions on the Internet?
Model 9: IPv6
Questions
- How big is an IPv6 address? How many such addresses are there?
- What is the purpose of the Flow label?
- How is an IPv4 address represented by an IPv6 address?
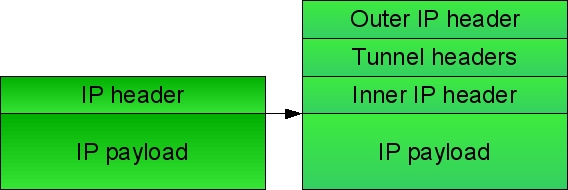
Model 10: Virtual Private Networking (VPN) and Tunneling
Questions
- From the perspective of the network, what is a tunnel?
- How might a tunnel be used to send IPv6 traffic over a network that involves transiting IPv4 nodes and networks?
- How might a tunnel be used to connect a computer to a local corporate network (i.e., a VPN)?